CYBER SOLUTIONS
Cyber Solutions

Transform your security program with solutions from the
largest enterprise security provider
Most preferred solutions
Most preferred solutions
IAM solutions
Cloud security solutions
Ransomware solutions
Cyber security solutions
AI cybersecurity solutions
Data security and protection solutions
Mobile security solutions
Unified endpoint management solutions
Security platforms
Cloud security platform
IBM Security SOAR platform
IBM Security SIEM platform
For more information, please contact us.


Transform your security program with solutions from the largest enterprise security provider
Most preferred solutions
Most preferred solutions
IAM solutions
Cloud security solutions
Ransomware solutions
Cyber security solutions
AI cybersecurity solutions
Data security and protection solutions
Mobile security solutions
Unified endpoint management solutions
Security platforms
Cloud security platform
IBM Security SOAR platform
IBM Security SIEM platform
For more information, please contact us.



Strengthen Your Cyber Resilience and adapt your security intelligently.
Developing human intelligence with machine intelligence
Artificial intelligence and machine learning (AI/ML) are important contributors to effective cyber resilience. With the vast amount of data generated by security solutions, the use of systems that can analyze behavior and risk and automate the response can dramatically increase an organization’s ability to intelligently adapt to vulnerabilities and attacks.
Discover, protect and secure sensitive and high-value data
Ensuring data security is the primary component of both cybersecurity and cyberresilience. This includes data in both structured and unstructured formats. To stay compliant with privacy and other government regulations, you need to be able to analyze the data you have and gather important insights.
Quickly build secure software with a holistic application security platform
Application security starts in your application development process. Testing needs to be scalable, flexible on-premises or on-demand, and integrated with your DevOps. It should include developer-friendly processes and be easily navigated through the code.
Centrally manage identities for all users, devices, objects and services
Identity and access management is the ability to manage “who” (employees, customers) and “what” (devices, services) accesses your systems and data. It allows you to develop trusted identities with the right level of access. Knowing the normal patterns of these identities makes it easy to identify when abnormal patterns occur.
For more information, please contact us.

Strengthen Your Cyber Resilience and adapt your security intelligently.
Developing human intelligence with machine intelligence
Artificial intelligence and machine learning (AI/ML) are important contributors to effective cyber resilience. With the vast amount of data generated by security solutions, the use of systems that can analyze behavior and risk and automate the response can dramatically increase an organization’s ability to intelligently adapt to vulnerabilities and attacks.
Discover, protect and secure sensitive and high-value data
Ensuring data security is the primary component of both cybersecurity and cyberresilience. This includes data in both structured and unstructured formats. To stay compliant with privacy and other government regulations, you need to be able to analyze the data you have and gather important insights.
Quickly build secure software with a holistic application security platform
Application security starts in your application development process. Testing needs to be scalable, flexible on-premises or on-demand, and integrated with your DevOps. It should include developer-friendly processes and be easily navigated through the code.
Centrally manage identities for all users, devices, objects and services
Identity and access management is the ability to manage “who” (employees, customers) and “what” (devices, services) accesses your systems and data. It allows you to develop trusted identities with the right level of access. Knowing the normal patterns of these identities makes it easy to identify when abnormal patterns occur.
For more information, please contact us.


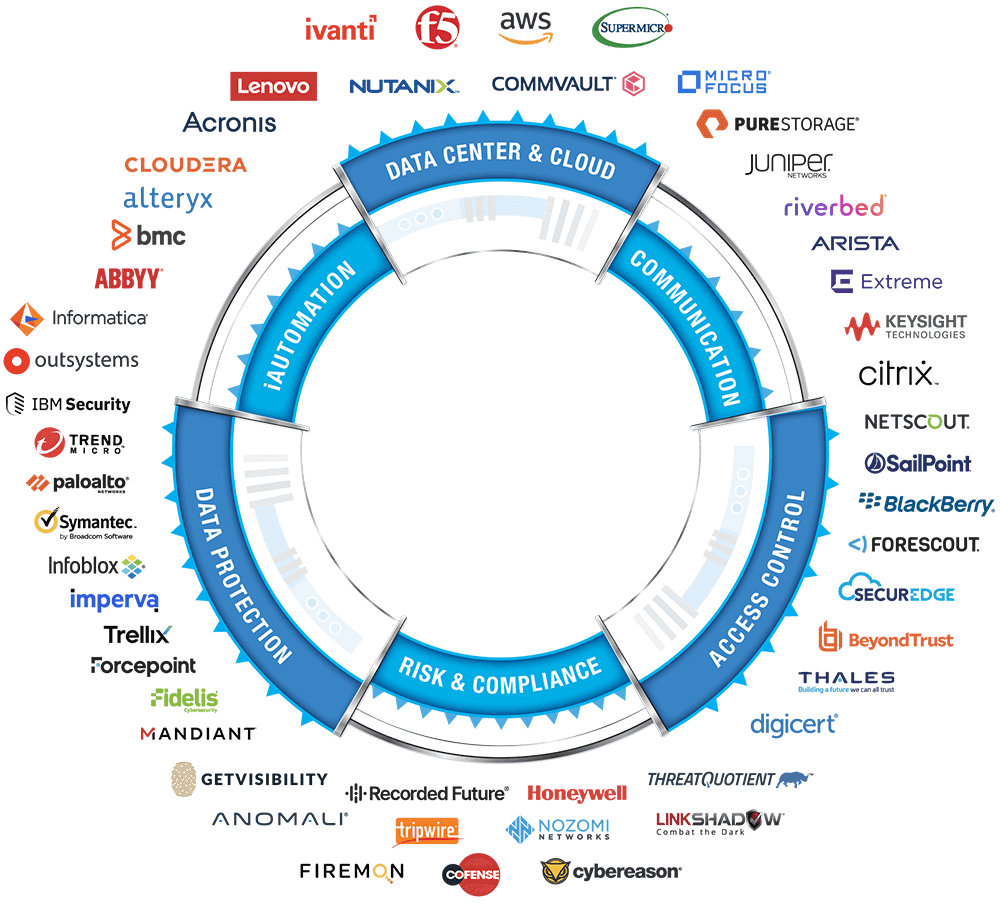
StarLink’s constantly evolving portfolio of niche technology solutions offers unique solutions in a variety of domains to address your IT Infrastructure and Cyber Security challenges.
StarLink helps customers stay profitable by providing integrated solutions in six key cybersecurity areas: Data Center and Cloud, Risk and Compliance, Data Protection, Access Control, Governance and Communication.
Where is your sensitive data located?
Protecting sensitive information from data theft and vulnerability is the priority of every organization. Whether on-premises or in the cloud, StarLink’s Data Center and Cloud portfolio helps you understand where your sensitive data should reside and how to intelligently protect it.
How is my sensitive data transmitted and where does it go?
Securely stored data is of no value if you cannot make it available when needed. Understanding your data environment, who and what is on the internal and external networks that access your applications and data is critical to making sure your data is accessed securely and in the most efficient way.
How and by whom is my data accessed?
Controlling access to your valuable data (in storage or in transit) is critical to ensure that only the right people and systems have access to it at any given time. Organizations with an ever-expanding digital landscape should adopt a multi-layered access control strategy with MFA, IAM, PAM, Secure Mobility and other solutions to prevent data breaches or abuse.
Is my sensitive data at risk or in compliance with the law?
Building a strong cybersecurity strategy is difficult without a solid GRC program. In addition, in certain countries and industries, strict regulatory compliance standards must be followed. StarLink’s GRC portfolio offers technology solutions that enable you to have a variety of components to scale, adapt and evolve as your business grows and regulations change.
Is my sensitive data well protected?
StarLink’s Data Protection portfolio offers comprehensive solutions across multiple environments that can protect your organization’s data throughout its lifecycle, reducing the risk of data exposure and simplifying operational complexity.
iAutomation
Smart Automation aims to empower businesses that want to create an automation-based digital transformation program with advanced technologies powered by Artificial Intelligence (AI) and automation to achieve greater productivity with lower cost, greater accuracy and improved customer experience. From Robotic Process Automation (RPA) to Artificial Intelligence (AI) and Advanced Analytics, the StarLink iA ecosystem can enable advanced automation and help organizations open up new possibilities for greater operational efficiency and business success.
For more information, please contact us.

StarLink’s constantly evolving portfolio of niche technology solutions offers unique solutions in a variety of domains to address your IT Infrastructure and Cyber Security challenges.
StarLink helps customers stay profitable by providing integrated solutions in six key cybersecurity areas: Data Center and Cloud, Risk and Compliance, Data Protection, Access Control, Governance and Communication.
Where is your sensitive data located?
Protecting sensitive information from data theft and vulnerability is the priority of every organization. Whether on-premises or in the cloud, StarLink’s Data Center and Cloud portfolio helps you understand where your sensitive data should reside and how to intelligently protect it.
How is my sensitive data transmitted and where does it go?
Securely stored data is of no value if you cannot make it available when needed. Understanding your data environment, who and what is on the internal and external networks that access your applications and data is critical to making sure your data is accessed securely and in the most efficient way.
How and by whom is my data accessed?
Controlling access to your valuable data (in storage or in transit) is critical to ensure that only the right people and systems have access to it at any given time. Organizations with an ever-expanding digital landscape should adopt a multi-layered access control strategy with MFA, IAM, PAM, Secure Mobility and other solutions to prevent data breaches or abuse.
Is my sensitive data at risk or in compliance with the law?
Building a strong cybersecurity strategy is difficult without a solid GRC program. In addition, in certain countries and industries, strict regulatory compliance standards must be followed. StarLink’s GRC portfolio offers technology solutions that enable you to have a variety of components to scale, adapt and evolve as your business grows and regulations change.
Is my sensitive data well protected?
StarLink’s Data Protection portfolio offers comprehensive solutions across multiple environments that can protect your organization’s data throughout its lifecycle, reducing the risk of data exposure and simplifying operational complexity.
iAutomation
Smart Automation aims to empower businesses that want to create an automation-based digital transformation program with advanced technologies powered by Artificial Intelligence (AI) and automation to achieve greater productivity with lower cost, greater accuracy and improved customer experience. From Robotic Process Automation (RPA) to Artificial Intelligence (AI) and Advanced Analytics, the StarLink iA ecosystem can enable advanced automation and help organizations open up new possibilities for greater operational efficiency and business success.
For more information, please contact us.

Contact us
Please let us know
how we can assist
Secureway’s business philosophy is to provide the highest quality innovative solutions, total customer satisfaction, timely delivery of solutions and the best price performance available in the industry.
Our mission is to help you improve your security performance, reduce risks, make you more productive, less stressed and a little more confident.
Contact Form
Contact us
Please let us know
how we can assist
Secureway’s business philosophy is to provide the highest quality innovative solutions, total customer satisfaction, timely delivery of solutions and the best price performance available in the industry.
Our mission is to help you improve your security performance, reduce risks, make you more productive, less stressed and a little more confident.
